Summary
This section systematically describes basic efforts and software quality technology in the DX process while companies are promoting DX to create and flexibly modify new business models that utilize new digital technologies. Finally, we will describe the current issues for ensuring quality in promoting DX.
1.Introduction
This article is a reprint of an article published in the journal Professional Engineer, April 2022.
DX is defined by the Ministry of Economy, Trade and Industry’s DX Promotion Index (*1) as “the transformation of products, services, and business models based on the needs of customers and society, as well as the transformation of operations themselves, organizations, processes, corporate culture and climate, to establish competitive advantage by utilizing data and digital technology in response to rapid changes in the business environment. DX is defined as “establishing competitive advantage by transforming products, services, and business models based on the needs of customers and society, as well as transforming operations themselves, organizations, processes, corporate culture and climate.
In other words, DX requires the creation of new value for customers and society, and the quality for value has shifted from the conventional bland quality (*2) to the integrated quality (*2) that has value for customers and others throughout the entire life cycle, and the attractive quality (*2) that exceeds satisfaction. To satisfy these qualities, it is important to utilize a combination of basic quality technologies. This paper describes basic approaches and software quality techniques that are useful for DX promotion.
2. Basic approach in DX process
2.1 The Case of Process
The following is a case study of an operating company. After developing the overall concept, business model reform and modernization of existing systems will be implemented.
(1) Overall Concept Formulation Phase
Establish a system with management and business divisions, etc., and formulate a vision, analyze the current situation, create a future ideal state, identify issues, conduct PoC, define requirements, etc.
(2) Business model transformation phase
Business divisions build business systems and billing models with stakeholders and develop services. The IT department will also build a digital platform and develop microservices to support the business department’s service development.
(3) Existing System Modernization Phase
Business divisions will standardize and review their systems in line with business model changes. IT departments will also modernize legacy systems.
2.2 Basic Approach
(1) Creating an environment for casual conversation
In the initial phase, there is often no knowledge of advanced digital technologies and the value they bring. As a result, discussions about what the future should look like sometimes end up at the level of modifying existing systems. Therefore, it is important to create an environment where business divisions can easily consult with the IT division and generate ideas.
(2) Create a mechanism to raise awareness of DX initiatives
Business divisions that are well versed in customer trends should take the initiative in promoting DX. However, business model reforms and operational reviews involve a lot of interest adjustment among stakeholders, which may reduce motivation. Therefore, it is important to create a mechanism to ensure that DX efforts are recognized throughout the company and that they lead to increased motivation.
(3) Start with clear objectives
It is easy to think that any information related to business should be converted into data. However, this may result in difficulty in finding data necessary for services, or in the inability to utilize other important data due to the maintenance of unimportant data. Therefore, it is important to analyze the scene of data utilization in 5W1H and proceed from the point where the purpose is clear.
3. Phase by phase software quality techniques
From the viewpoint of quality creation, software quality techniques for each phase are described (Fig. 1, Fig. 2, and Fig. 3).
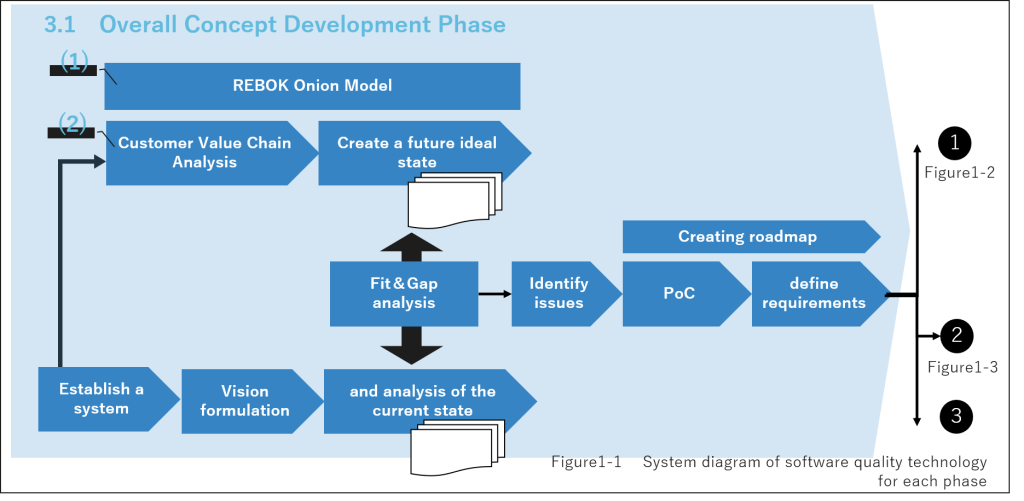
3.1 Overall Concept Development Phase
Stakeholder identification and value analysis are important for companies. We describe the following two techniques that can effectively extract them without omissions.
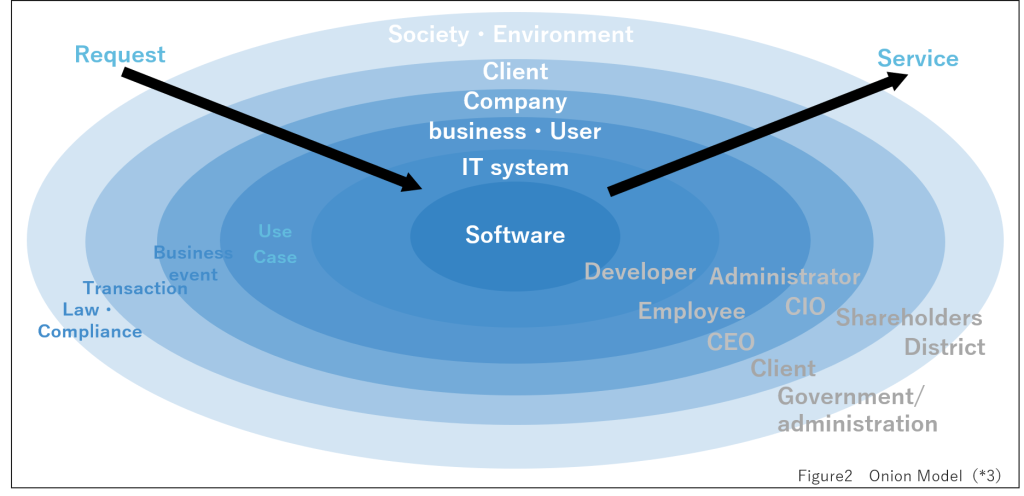
(1) REBOK Onion Model(*3) (Figure 2)
The REBOK is a requirements engineering knowledge system that organizes and systematizes the knowledge that serves as a guide for utilization from a practical perspective. The onion model is a technique for stakeholder identification of REBOK’s requirements acquisition techniques. It places the software to be realized at the center of an ellipse and visualizes the stakeholders who influence it from the center outward. It can also be utilized by placing the service or product at the center of this ellipse.
(2) Customer Value Chain Analysis (*4)
Customer value chain analysis is a technique to visualize what kind of value is provided from whom to whom by identifying all stakeholders and organizing the exchange of money and information among stakeholders in order to identify the true customers for the service or product to be realized.
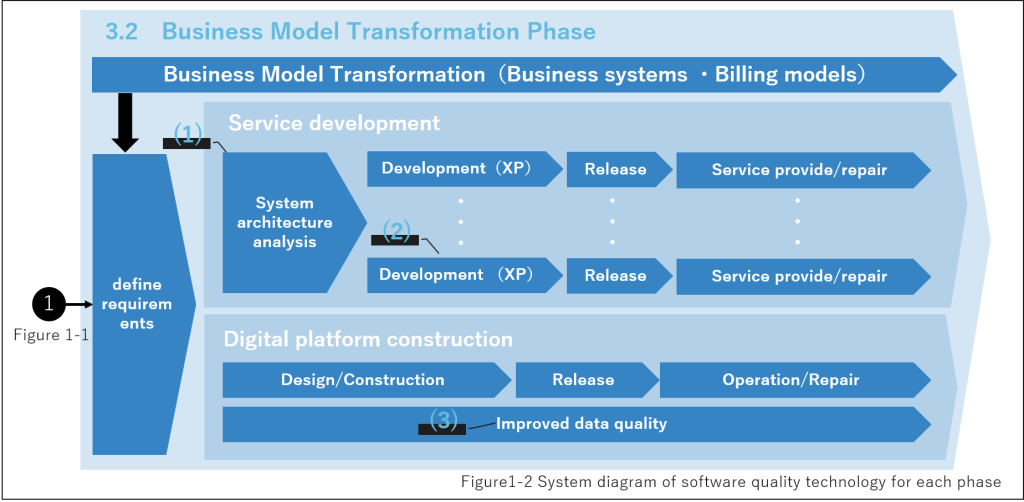
3.2 Business Model Transformation Phase
(1) System architecture analysis (*5)
Service development is conducted by defining requirements based on stakeholder demands. System architecture analysis is a technique to extract functions to be developed without omission. This is a technique to decompose requirements-defined functions into parts and processes into time axes, and to clearly define the means to realize each decomposed function.
(2) Extreme Programming(*2)
In service development, development is conducted toward the ideal future state. In this case, development is done in an agile style, where development is done in units of small services. The following three techniques of Extreme Programming, which most reflect the concept of building quality among agile methods, are described.
(2-1) Test-driven development (*2)
In Test Driven Development, from the viewpoint of writing only the necessary code, test code for testing is written first, followed by the application code. Then, tests are repeatedly executed in the process of completing the application code, and refactoring is performed to refine the application code as it passes the tests. This technique improves maintainability because the application code can be written at an appropriate level of abstraction through refactoring. In addition, since the test code can be used many times, it is effective in a continuous delivery environment where source code is modified and released daily.
(2-2) Refactoring (*2)
Refactoring is the process of changing the internal structure of software to improve software maintainability while maintaining the behavior of the service from the customer. For example, software that contains many unnecessary comments, code clones, huge class structures, too long method structures, complex code with many conditional branches, etc. are subject to refactoring.
(2-3) Pair Programming (*2)
Pair programming is a technique in which two people develop a single program. While one person writes the program source code, the other person checks the code and refines it. In addition to quality improvement, development knowledge and skills can be shared, preventing the use of a single person. Research has shown that the productivity of pair programming is only about 15% lower than that of two people programming separately.
(3) Improvement of data quality
It is important to improve the quality of data so that it is easy to use when utilizing data in services. The following two techniques are effective in this regard.
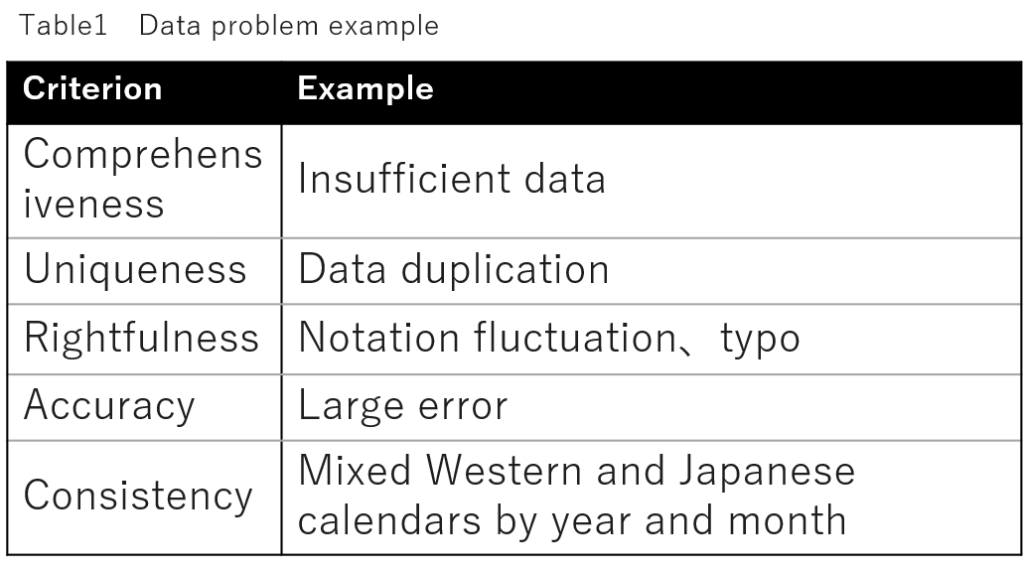
(3-1) Utilization of data quality model characteristics
Data to be collected on digital platforms may have the following problems (Table 1).
Therefore, at the time-of-service development, correction and naming of these data should be performed with reference to various documents (*2,*6,*7), etc. In addition, a mechanism for data operation after service release should also be established.
(3-2) Maintenance of data catalogs (*8)
A data catalog clarifies the location and contents of data to facilitate understanding and discovery of data. This will enable users to obtain the data they need when they need it. It is important to establish a common format for data catalog items to make the existence of data more widely recognized throughout the ecosystem. The use of a common format will facilitate the coordination of data catalog information with the data catalogs of stakeholders in the ecosystem and increase awareness of the existence of data.
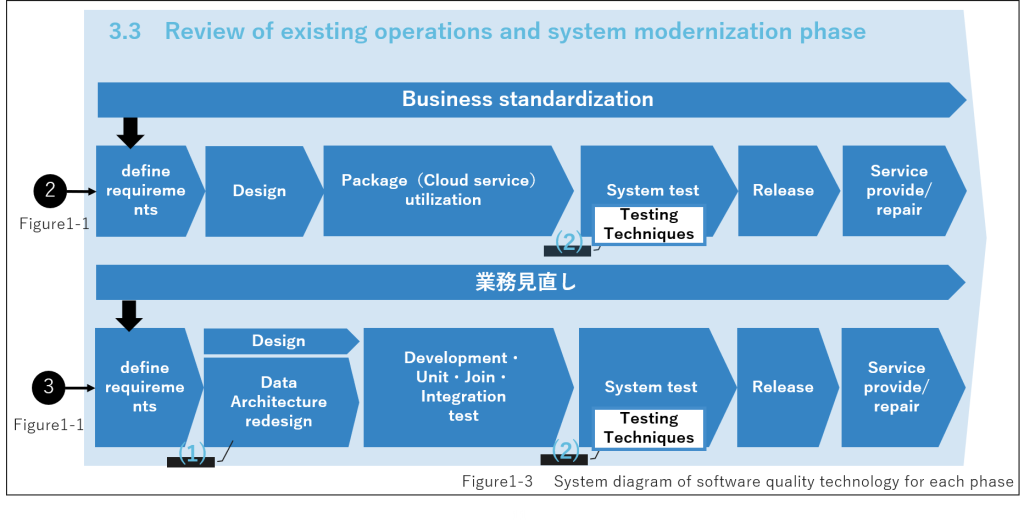
3.3 Review of existing operations and system modernization phase
(1) Data Architecture Redesign
The modernization of existing systems combines the use of packages with business standardization and business review to improve maintainability. Many databases, which are at the core of these systems, were designed with the concept of one fact in one place, and multiple systems are tightly coupled in a spaghetti-like intertwined manner. This was appropriate in the era of host computers, which required centralized data governance, but is problematic for maintainability in the modern era. Therefore, we should redesign where data should be placed and when it should be delivered to users, in light of the business and stakeholders in the current and future ideal state. In other words, the maintenance is improved by identifying the timing when data consistency is always required in the business and designing a moderate loose coupling based on that.
(2) Testing Techniques
It is difficult to cover 100% of stakeholders’ requirements in system testing to confirm quality. The following two testing techniques are effective in confirming the existence of defects and detecting defects in high-risk events. These techniques can also be used in other phases of system testing.
(2-1)Risk-Based Testing (*2)
Risk-based testing is a testing technique that assumes situations in which software defects that may affect services are likely to occur and confirms whether these defects actually occur. Based on risk analysis, testing can be performed with priority on those with large risks.
(2-2) Combination testing of a small number of factors (*2) Combination testing is a testing technique to determine the combination of test conditions. Here, a factor refers to an item to be tested and a level refers to a value that an item can take. Some research reports indicate that most software defects occur when the number of factors is small, such as two factors. This is done using an orthogonal table, etc.
4. current issues to ensure quality
4.1 Establishment of third-party platform selection
The use of third-party platforms such as cloud services is essential for DX. However, there are risks involved in using these services because quality assurance methods have not yet been established, and the establishment of selection methods for these services is an issue. For example, when using cloud services in the current situation, the basic policy for the use of cloud services in government information systems (*9) is used as a reference to select cloud services that can be judged to minimize business risks based on information on operational performance, business continuity, security measures, and compliance with legal systems/standards, etc. In many cases.
4.2 Provide value to customers and others throughout the lifecycle
Once a service is released, it is necessary to monitor whether it continues to provide value to customers and to continuously provide value through improvements. To this end, it is necessary to establish KPIs such as service level indicators and quality evaluation indicators for customer use and establish a mechanism to guarantee continuous value provision throughout the customer lifecycle.


